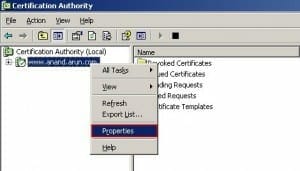
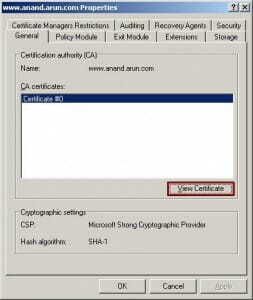
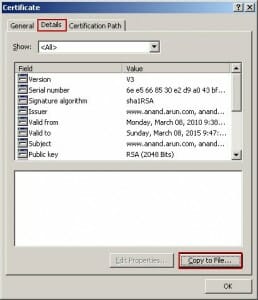
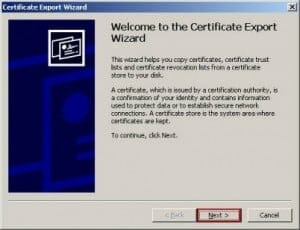
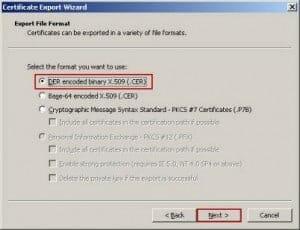
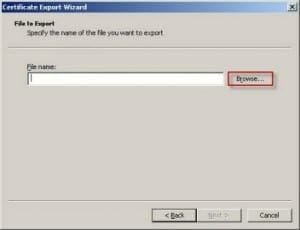
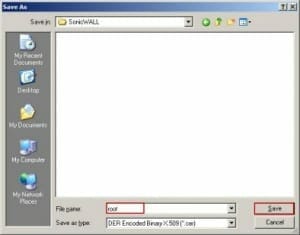
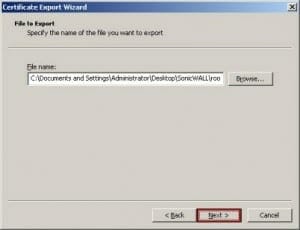
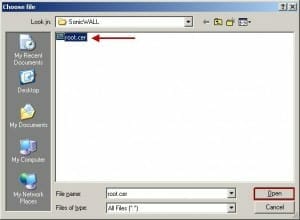
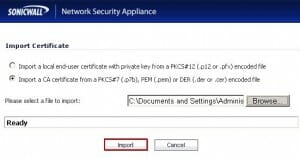
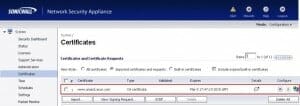
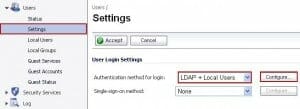
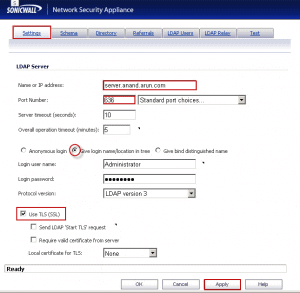
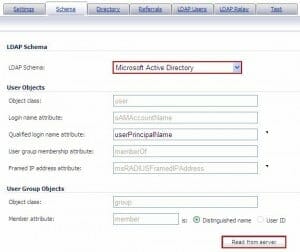
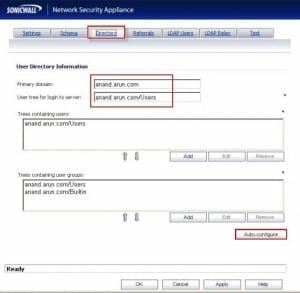
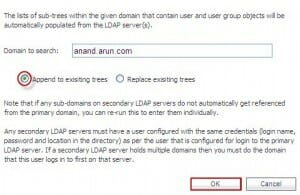
The Acumen IT Support blog provides you with helpful articles about the Microsoft Active Directory.
Microsoft Active Directory provides user and computer security for your Windows computers. Like a phonebook stores information about people, Active Directory stores information about your network’s components.
Several web sites provide good overviews.
Official Microsoft Overview
Active Directory Wikipedia